Adding SSO to MyAccessLive will also give enterprises to gain full visibility and control of user access, across all applications. It uses a standards-based framework and comes with pre-built connectors, according to Aveksa’s Chief Technology Officer Deepak Taneja.
Aveksa Adds SSO to Its Cloud-Based Identity, Access Management SaaS Platform
Installing OpenAM
On this post we’ll show you some screen about the process. The installation was executed using Tomcat 7
After you deployed the opensso.war you need to go to the browser to install the installation.
Go to the http://localhost:80/opensso and you’ll see the screen to start the installation for OpenAM. Here you can choose for a Create a Default Configuration or Create New Configuration. For this example we’ll choose Create a Default Configuration
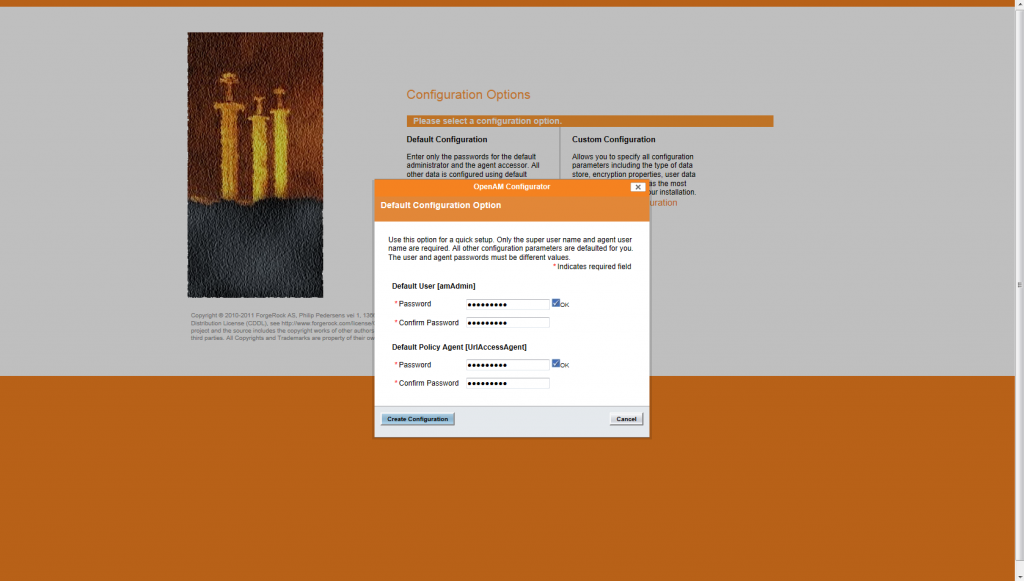
After you select the default configuration, a screen appears to introduce the password for the openAM default users and default policy agent. Here introduce a password and click Create Configuration
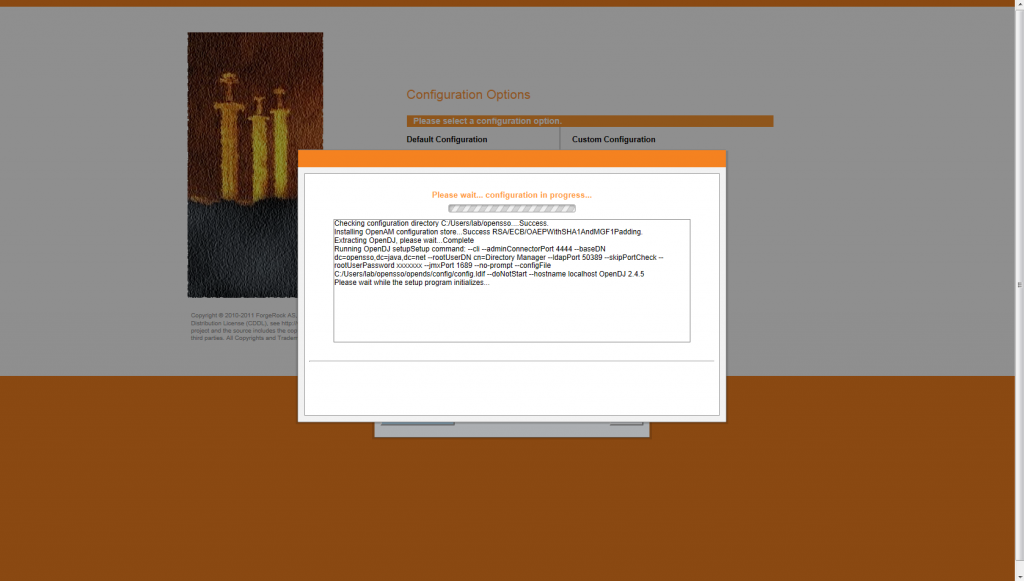
At this point OpenAM we’ll start the installation process and wait windows is displayed.
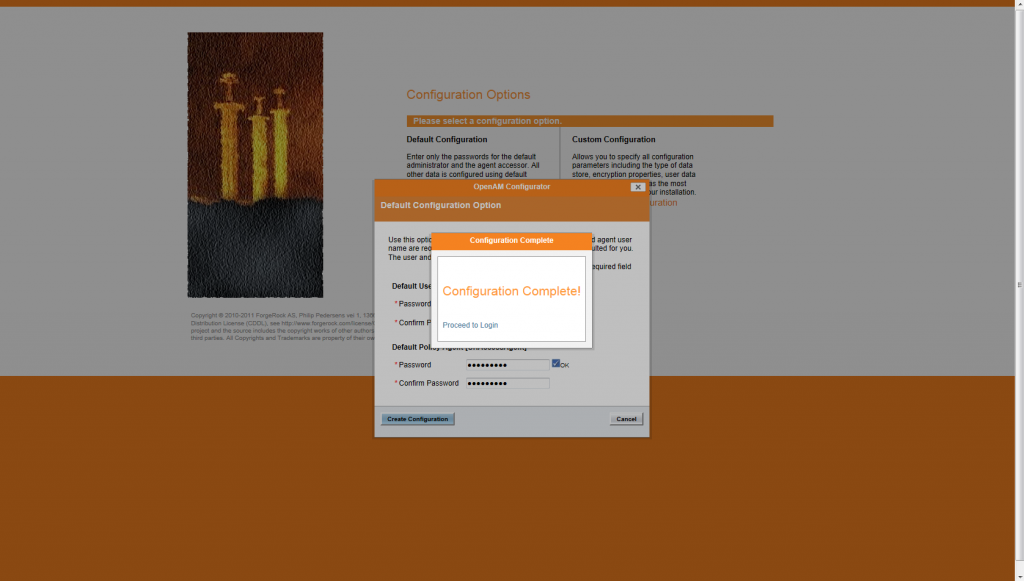
Once the OpenAM installation and configuration is completed, you’ll see a window with a Configuration Complete message. You can click on the proceed to login button to start using the OpenAM instance.
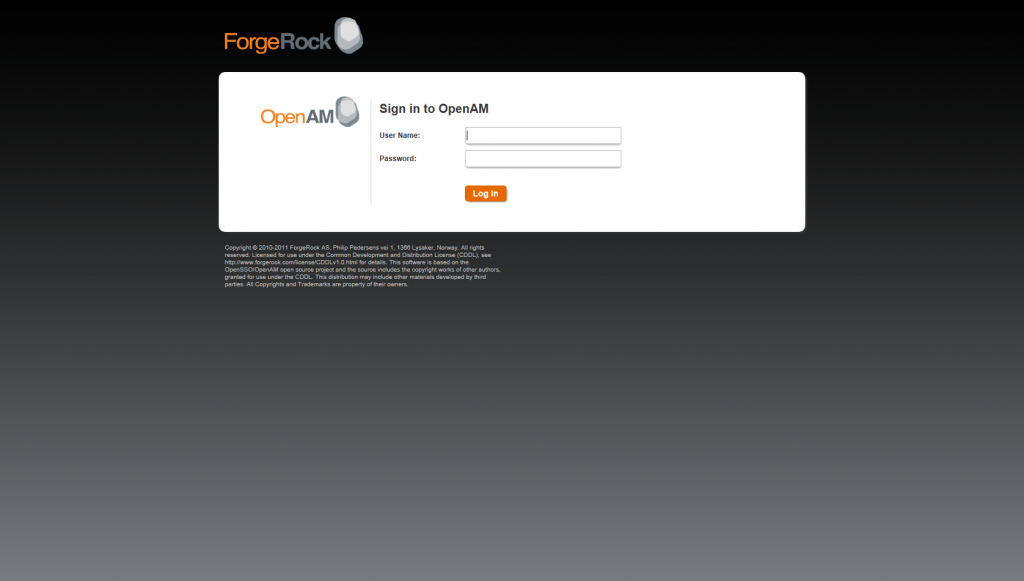
On the Sign In to OpenAM page you’ll need to introduce the credentials to access to the configuration screens. You can use the default OpenAM user name account called amAdmin with the password you introduced during the installation.
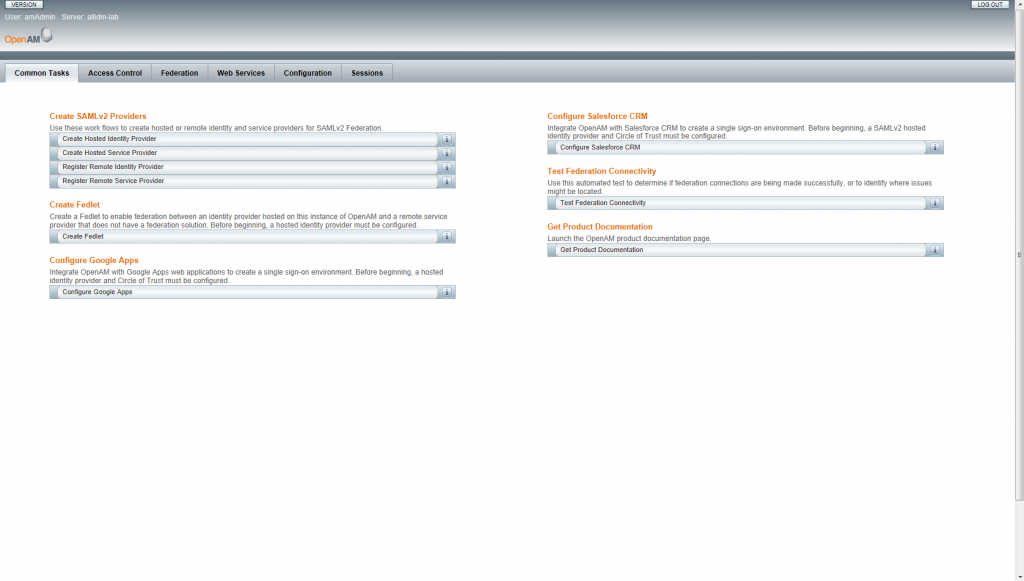
If the credentials were properly introduced, openAM will allow you to login and load the common task tab with some recommended initial tasks.
You can learn more about OpenAM on the Forgerock website
Quest One Identity Manager in few words
Q1IDM is a product based on a database driven due that Information such as employee properties, information about user accounts and organizational data are stored in the database. Q1IDM works together with Microsoft SQL Server and Oracle database systems.
Also, access permissions data, workflow definitions, parameters for influencing and controlling system behavior and data for customizing Identity Manager administration tools to suit the user’s needs are also stored in the database.
Some of the technologies related to the quest one identity management product are:
• Microsoft Windows Server
• Microsoft SQL Server ( or Oracle Database )
• Microsoft IIS
• Microsoft Visual Studio (mainly VB and C#)
OpenIDM 2.1 now released and available
discovery engine enables the organization to synchronize users across many different data stores to ensure records are accurate and up to date in support of compliance and audit requirements. OpenIDM 2.1 embeds the Activiti Business Process and Workflow engine, a comprehensive, lightweight, and scalable solution, which meets industry-standard Business Process Model and Notation (BPMN) version 2.0 compliance, to support workflow-driven provisioning and identity management.
Take a look on theOpenIDM 2.1.0 Release Notes here http://docs.forgerock.org/en/openidm/2.1.0/release-notes/index/index.html
Take a look on the OpenIDM project here http://openidm.forgerock.org/
Calculate the initial database size in quest One Identity Manager (Q1IM)
Initial quest one database size is based on the employees, here some recommended sizes:
* 1 GB – Test database
* 5 GB – 1000 employees
* 10 GB – 10000 employees
* 20 GB – 20000 employees
* 50 GB – 50000 employees
* 100 GB – 100000 employees
NetIQ Self Service Password Reset (SSPR) at Glance
Some of the features provided by the SSPR are:
* Stand-alone, easy to deploy, java web application
* Captcha support using reCaptcha
* Change current password
* Challenge response setup
* Reset forgotten password:
* New user registration
* Simplify help desk support response
* Localized for Czech, Dutch, English, French, German, Italian, Polish, Portuguese, Spanish
* Support for large dictionary wordlists to enforce strong passwords
The product bits are very light. If you want to install the product you need the next prerequisites:
* Java JDK
* Apache Tomcat
* SSPR War file
The sspr installation allow you to do the configuration in three different ways
* New Configuration – Novell,OpenLDAP,DirectoryServer389,Others
* New Configuration – Active Directory – Store responses in a database
* New Configuration – Active Directory – Store responses Active Directory
The installation process is not complicated after you download the product you’ll need to:
1. deploy the sspr.war
2. Setup some schemas on your directory server
3. Go to the Config Manager and complete the configuration
a. http://localhost:7080/sspr/config/ConfigManager
4. Start using the product
You can download from here and learn more about the NetIQ Self Service Password Reset ( SSPR )
Open Source Directory Server OpenDJ
OpenDJ is open source LDAPv3 compliant directory service, developed for the Java platform, providing a high performance and secure store for the identities managed by your enterprise.
Just for your history records OpenDJ is a downstream build of the OpenDS project, with a different name to avoid trademark issues. OpenDJ comprises of an open source directory server, client tools, and an LDAP SDK. All modules are 100% Java based and require at least Java 1.6.
You can download OpendDJ from http://forgerock.com/opendj-downloads/ the current version as we speak is the OpenDJ 2.5
Need a password manager solution. Quest One Password Manager
This product also includes Flexible Self-Service and Helpdesk Workflows.
If you are looking for Phone-Based Authentication quest one Password Manager offers the phone-based authentication that will allow users perform password management tasks on the Self-Service site, after that they will receive an automated SMS or call to the phone number on record with a one-time PIN code. Then they will be required to enter the one-time PIN code on the Self-Service site to authenticate themselves.
Some tasks you can do on the project are:
* Policies Management
* Password Policies
* Reporting
* Password manager and backup recovery
* License control
You can take a look on the product web page to get more details http://www.quest.com/quest-one-privileged-password-manager/
Create a Root user in OpenDJ
You need to do two main steps:
1.Create the root user on OpenDJ
2.Change the root user created the privileges
a.Take a look on the OpenDJ documentation to identify what is available. About OpenDJ Privileges
Below is an example about how to do it, in order to complete it you need:
1.Copy the text below using a text editor and save it as a ldif file. For example runme.ldif
# Create root user
dn: cn=TestRootUser,cn=Root DNs,cn=config
objectClass: inetOrgPerson
objectClass: person
objectClass: top
objectClass: ds-cfg-root-dn-user
objectClass: organizationalPerson
userPassword: password
cn: TestRootUser
sn: TestRootUser
ds-cfg-alternate-bind-dn: cn=TestRootUser
givenName: Directory# Change a Root User’s Privileges
dn: cn=TestRootUser,cn=Root DNs,cn=config
changetype: modify
add: ds-privilege-name
ds-privilege-name: proxied-auth
ds-privilege-name: data-sync
2.On your openDJ instance, go to the bin or bat folder depending on your operating system and execute the next command.
On windows you can try something like:
ldapmodify -h localhost -p 389 -D “cn=Directory Manager” -w Password1dm –defaultAdd –filename “C:\Forgerock\OpenDJ\bat\runme.ldif”
Installing Oracle Unified Directory 11gR2
Steps to Install Oracle Unified Directory 11gR2
In this post we’ll show you some screen about the installation process for Oracle Unified Directory Server 11gR2.
1. Download the OUD and Unzip the OUD installable
2. Go to the unzipped folder and double click on the setup.exe file
3. On the welcome window click next

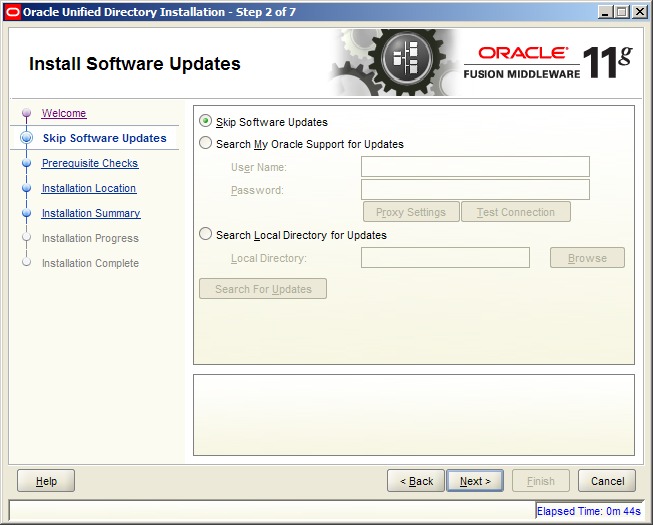
4. The Install software updates window is displayed; here you can provide your oracle support credentials. Select Skip Software updates
5. The Oracle installation for Oracle Unified Installation will check the prerequisites. Click Next

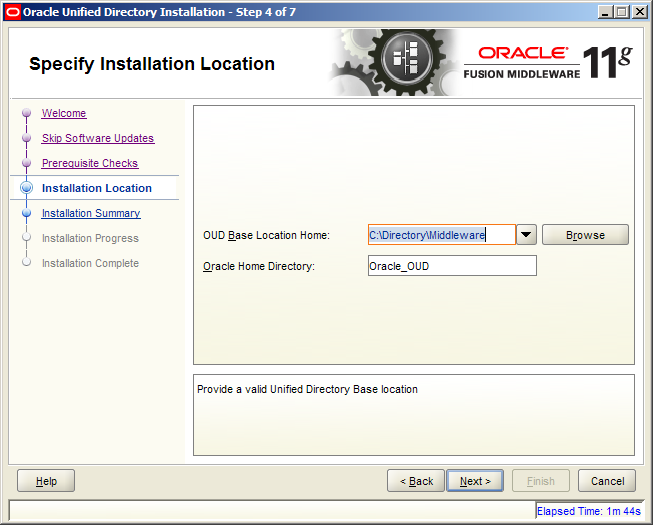
6. Specify the installation location. For this example we’ll create a brand new folder called Directory\Middleware, and specify the OUD instance name
7. The installation summary is displayed. Take a look and click next

8. The installation will start and you’ll see the installation progress bar at the top

9. Once is completed click next button

10. Now the installation is completed. Click the finish button and start working on the product

11. We recommend you to go back to the installation folder and explore the files installed
ManageEngine Launches Integrated IAM Solution for Windows Shops
In Windows environments, IAM means more than provisioning users. End users themselves must also be able to perform self-service tasks, which relieves the IT help desk of routine duties so that IT staff can concentrate on more demanding help desk chores. Similarly, the increasing demands of IT regulations are driving IT organizations to generate a growing number of reports to demonstrate compliance. While discrete, individual products can meet these demands on a point by point basis, they complicate IAM efforts with multiple management consoles, product configurations and sign on credentials.
Check the Article
Source Yahoo Finance
Check the product http://www.manageengine.com/active-directory-360/index.html
New Release of Quest One Quick Connect for Cloud Services 3.4
Look What’s New:
Quest One Quick Connect for Cloud Services connects to the following target systems:
- Google Apps
- Google Postini Services
- Microsoft Office 365
- Salesforce
- ServiceNow
Take a look on the Quest One Quick Connect for Cloud Services page
How to Integrate NetIQ Access Manager with ServiceNow IT Service Management Software
This cool solution will show you how to integrate ServiceNow into your NAM implementation using a federated authentication via SAML 2.0. By using SAML 2.0, your users authenticate to NAM as they typically do using their existing LDAP credentials provided by your corporate directory. The service-now.com application then authenticates users via SAML without the need to synchronize passwords with service-now.com.
Aveksa Adds SSO to Its Cloud-Based Identity, Access Management SaaS Platform
Adding SSO to MyAccessLive will also give enterprises to gain full visibility and control of user access, across all applications. It uses a standards-based framework and comes with pre-built connectors, according to Aveksa’s Chief Technology Officer Deepak Taneja.
Installing OpenAM
On this post we’ll show you some screen about the process. The installation was executed using Tomcat 7
After you deployed the opensso.war you need to go to the browser to install the installation.
Go to the http://localhost:80/opensso and you’ll see the screen to start the installation for OpenAM. Here you can choose for a Create a Default Configuration or Create New Configuration. For this example we’ll choose Create a Default Configuration
After you select the default configuration, a screen appears to introduce the password for the openAM default users and default policy agent. Here introduce a password and click Create Configuration
At this point OpenAM we’ll start the installation process and wait windows is displayed.
Once the OpenAM installation and configuration is completed, you’ll see a window with a Configuration Complete message. You can click on the proceed to login button to start using the OpenAM instance.
On the Sign In to OpenAM page you’ll need to introduce the credentials to access to the configuration screens. You can use the default OpenAM user name account called amAdmin with the password you introduced during the installation.
If the credentials were properly introduced, openAM will allow you to login and load the common task tab with some recommended initial tasks.
You can learn more about OpenAM on the Forgerock website
Quest One Identity Manager in few words
Q1IDM is a product based on a database driven due that Information such as employee properties, information about user accounts and organizational data are stored in the database. Q1IDM works together with Microsoft SQL Server and Oracle database systems.
Also, access permissions data, workflow definitions, parameters for influencing and controlling system behavior and data for customizing Identity Manager administration tools to suit the user’s needs are also stored in the database.
Some of the technologies related to the quest one identity management product are:
• Microsoft Windows Server
• Microsoft SQL Server ( or Oracle Database )
• Microsoft IIS
• Microsoft Visual Studio (mainly VB and C#)
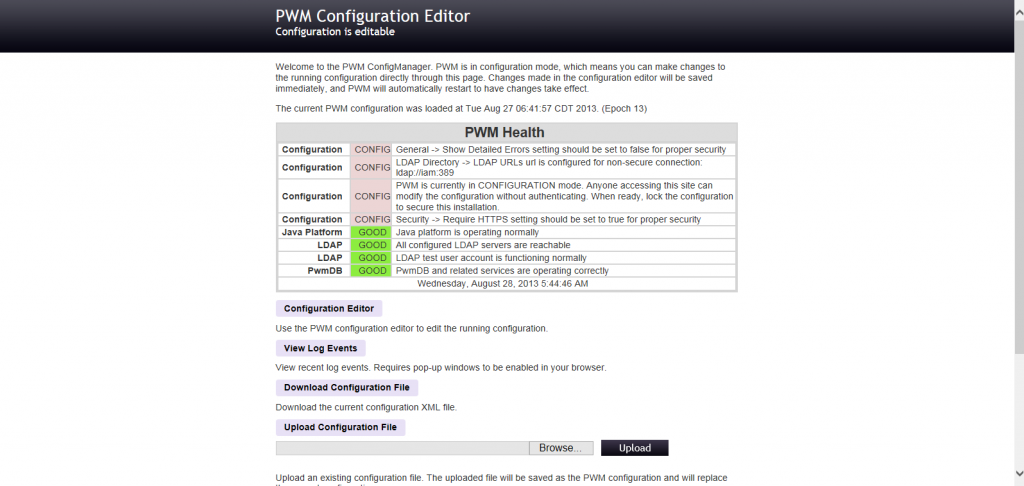
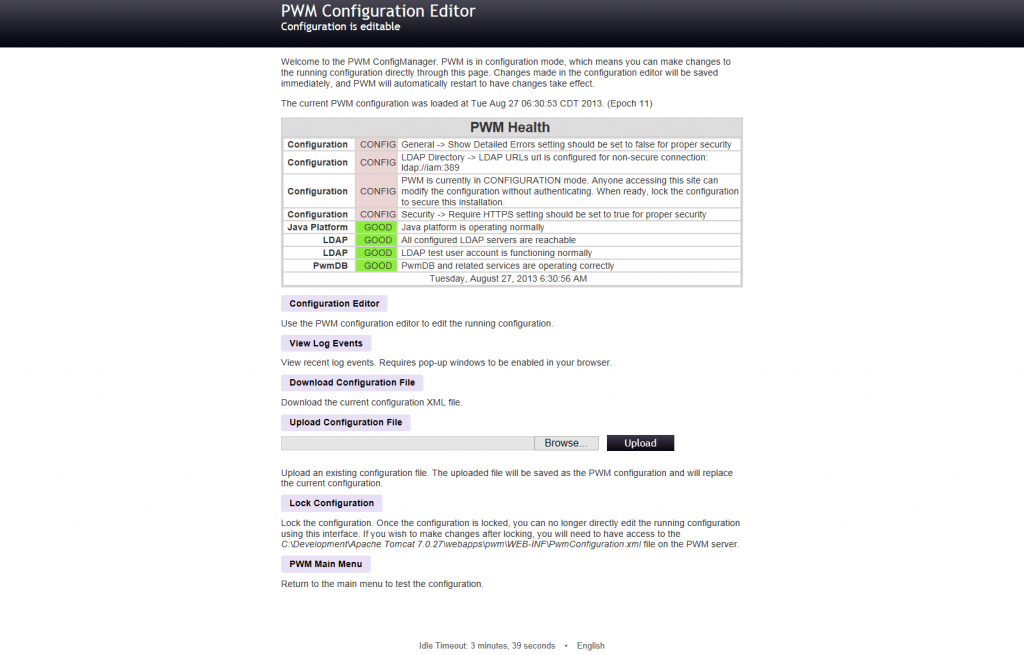
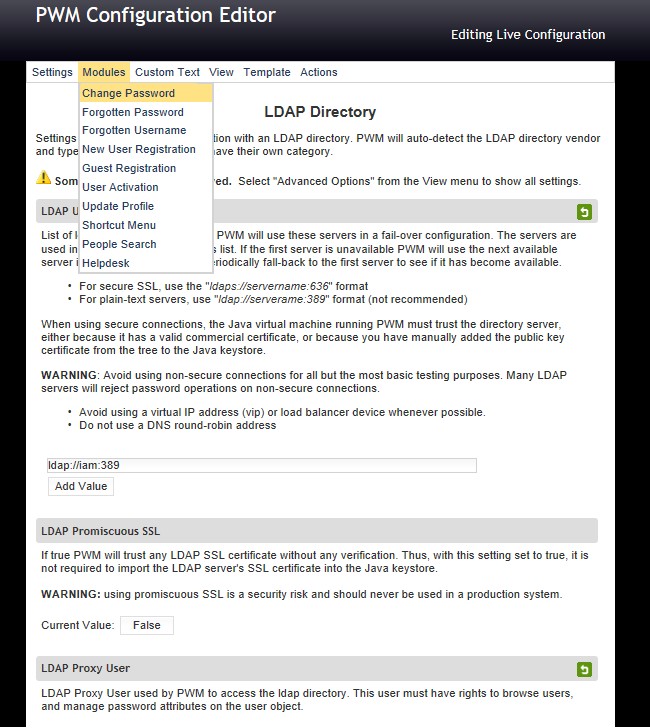
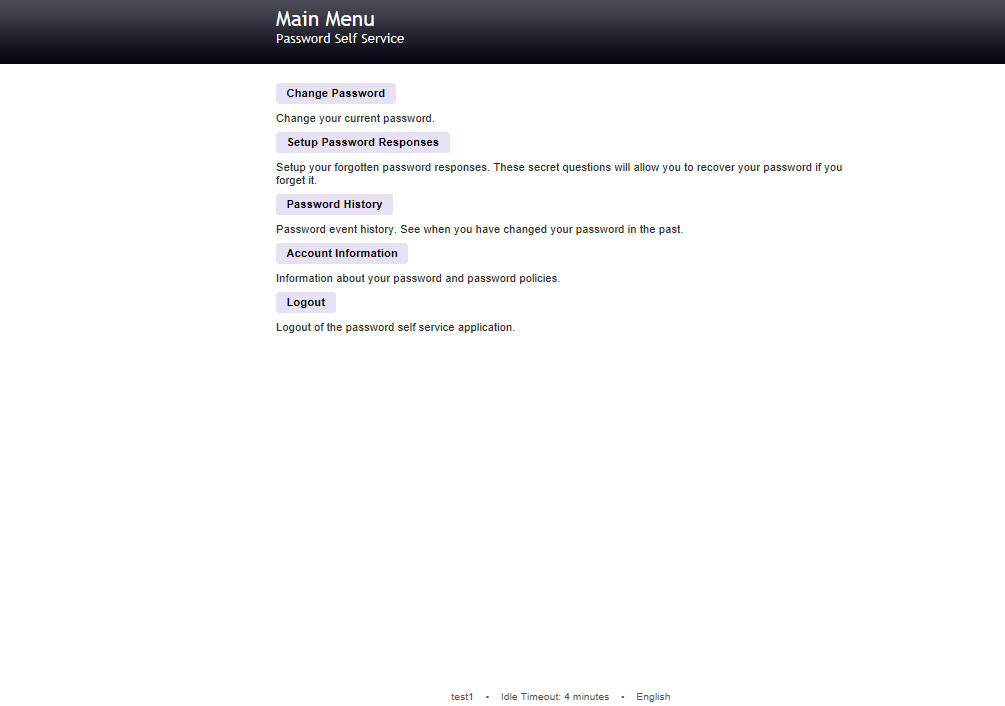
Configure Change Password in Open Source Password Self Service for LDAP directories (PWM)
Go to the Installation URL and select configuration editor.
http://localhost:8080/pwm/config/ConfigManager?
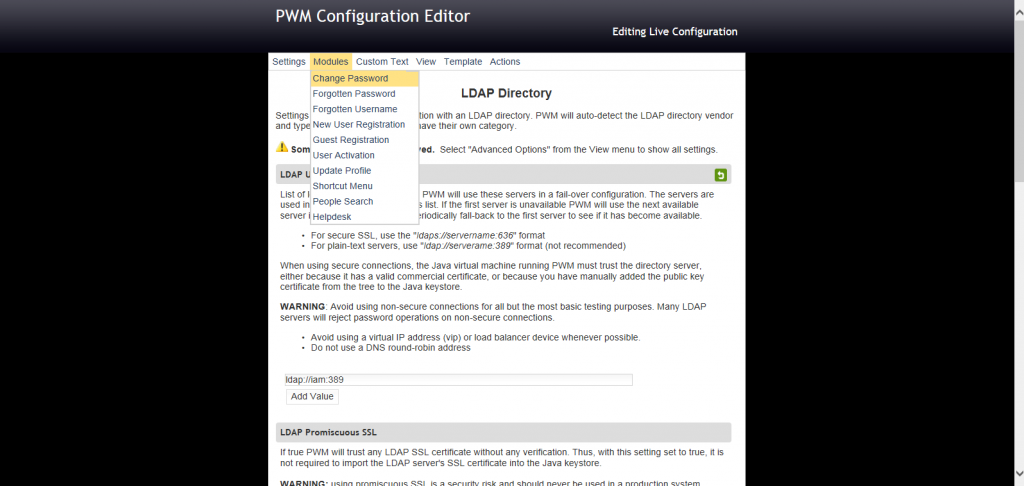
Select Modules and Change Password
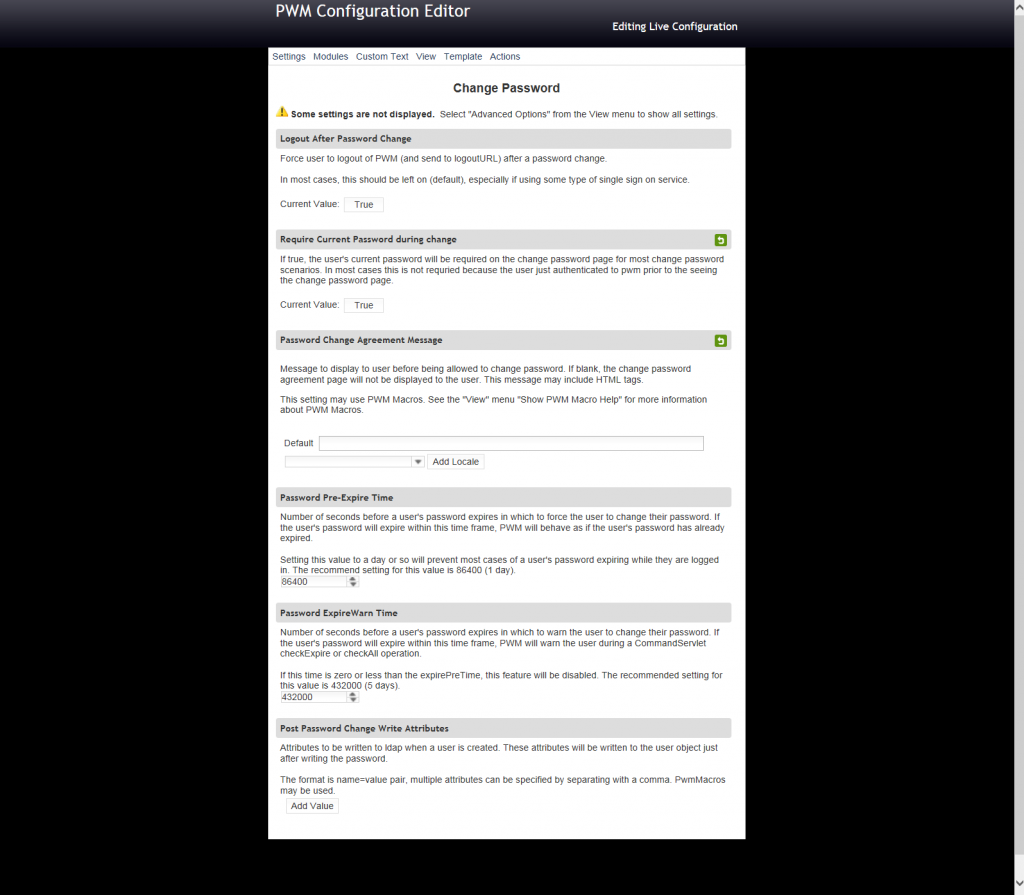
PWM will display a page with the different options allowed to configure.
Click the menu actions at the top and save your changes. At this point Password Manager Open Source tool will check everything is properly configured. Click the PWM main menu button at the bottom to return and test the configuration.
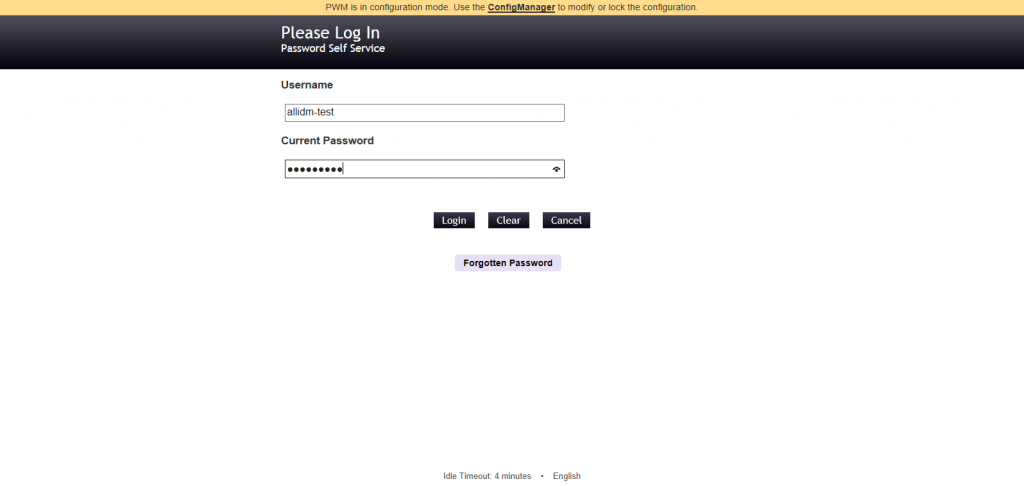
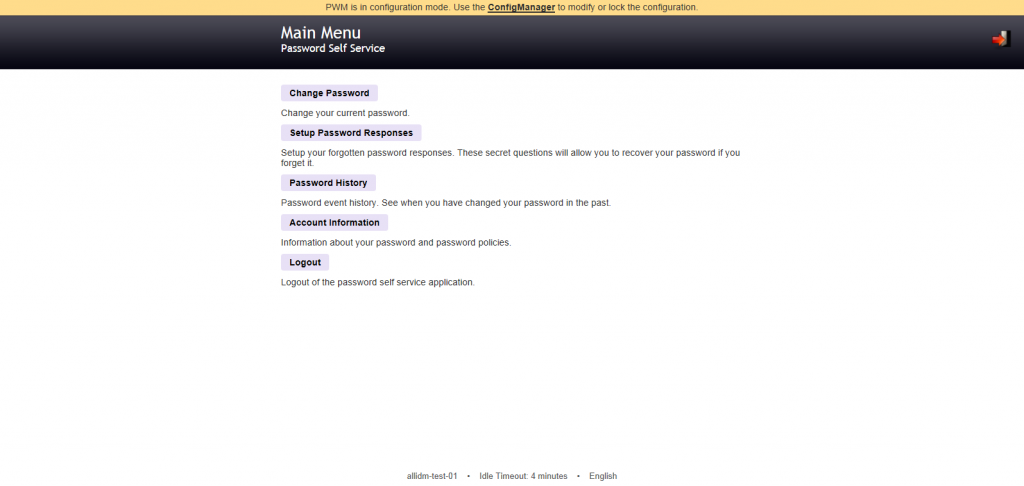
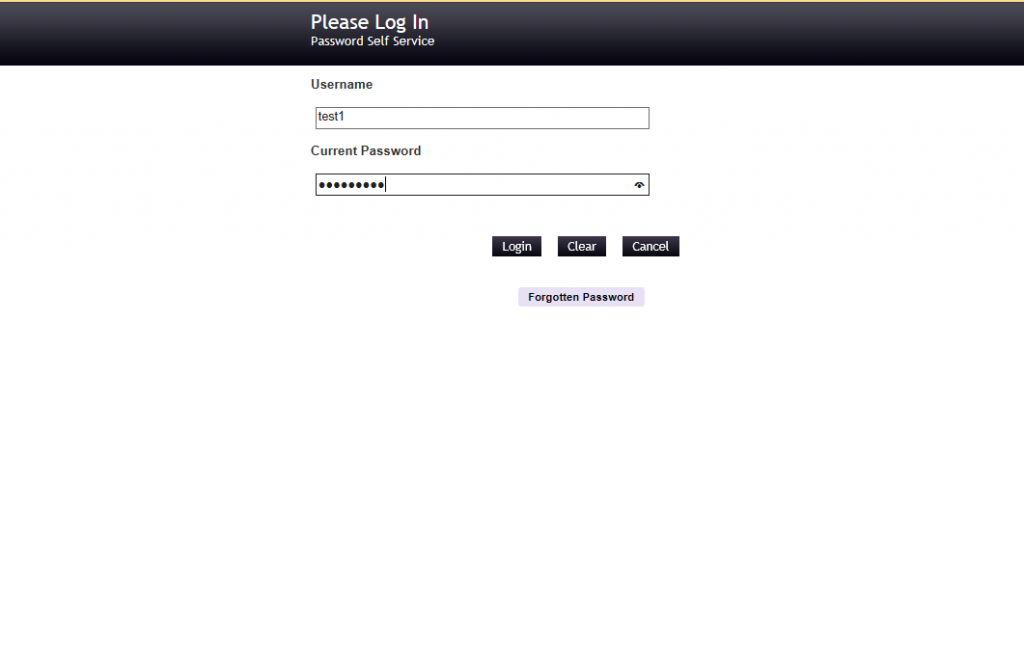
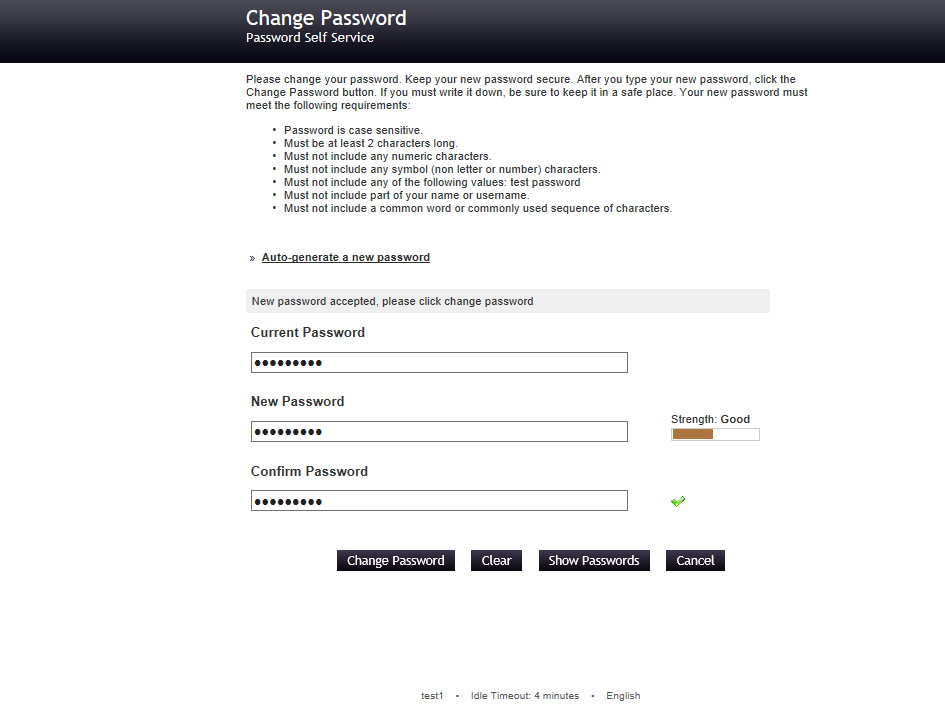
Testing Change Password in the Open Source Password Manager Self-Service
Login with a test user.
Select Change Password.
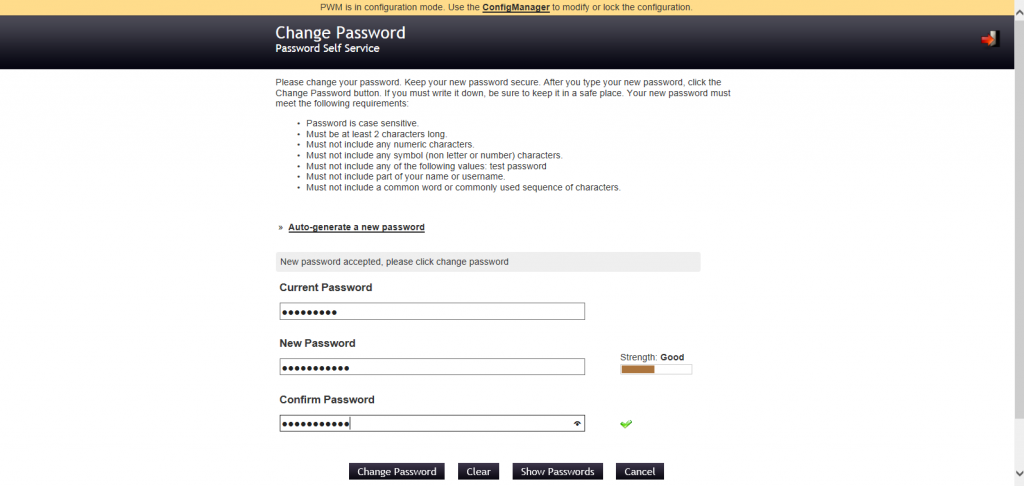
Introduce the Current Password and the new password and click change password button.
Here you can also click the Auto-generate a new password to get one.
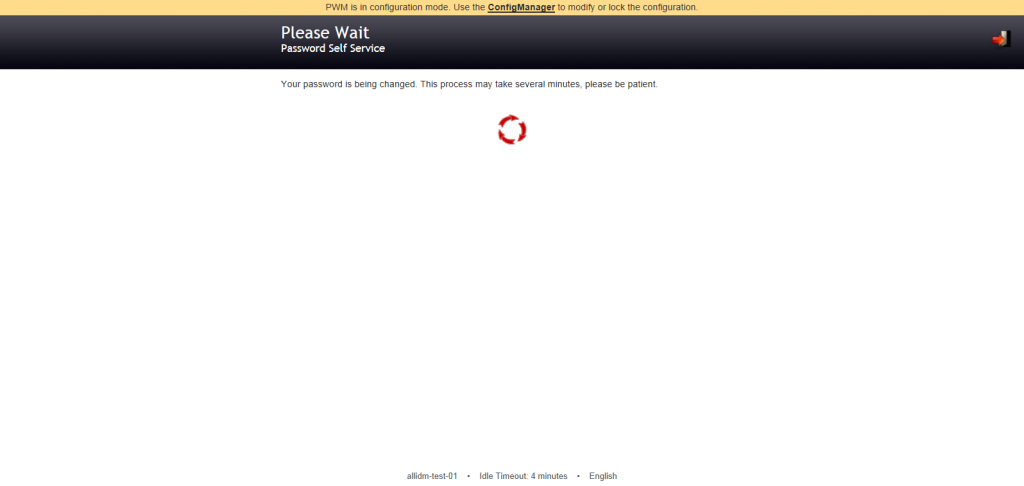
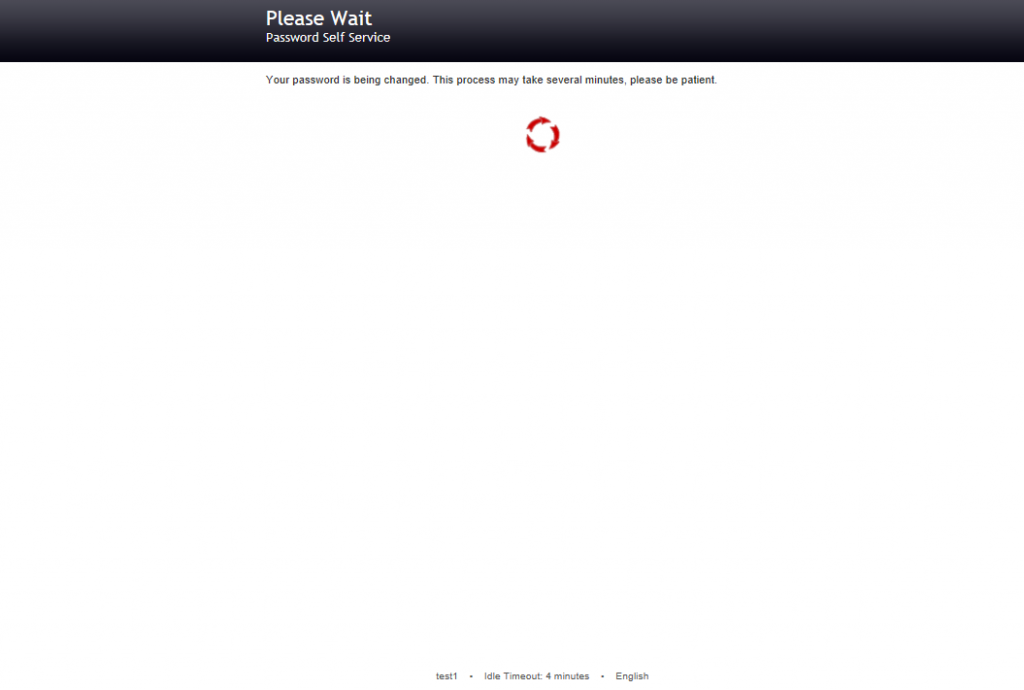
Wait meanwhile the Open Source Password Manager tool change your password.
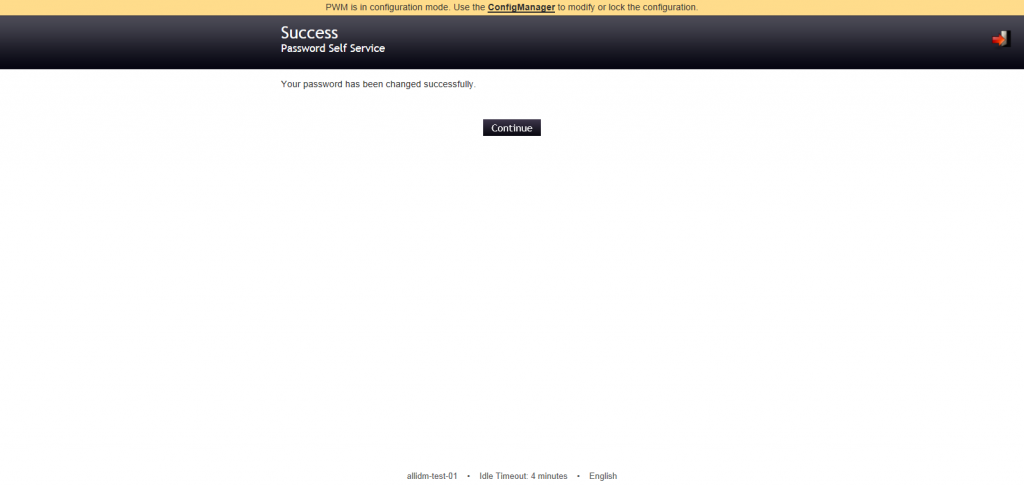
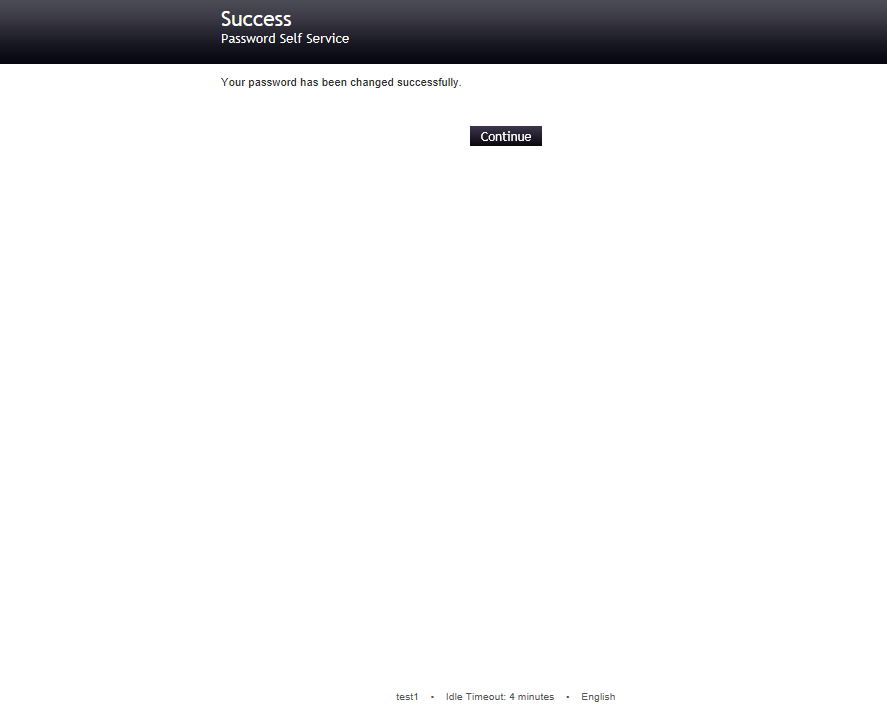
After a while PWM will display a successfully complete screen. Click continue.
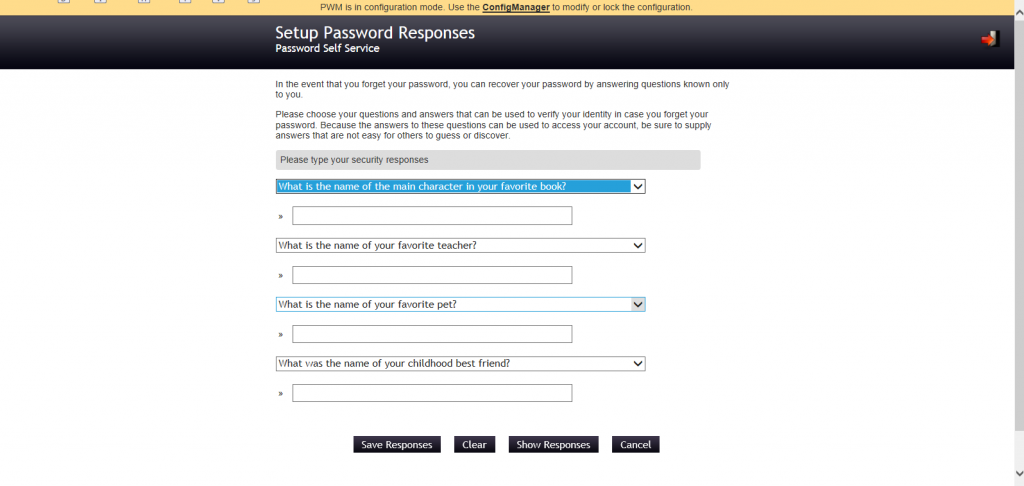
For new user that has never registered with the tool or change his password with the PWM the SETUP Password Response will be displayed.
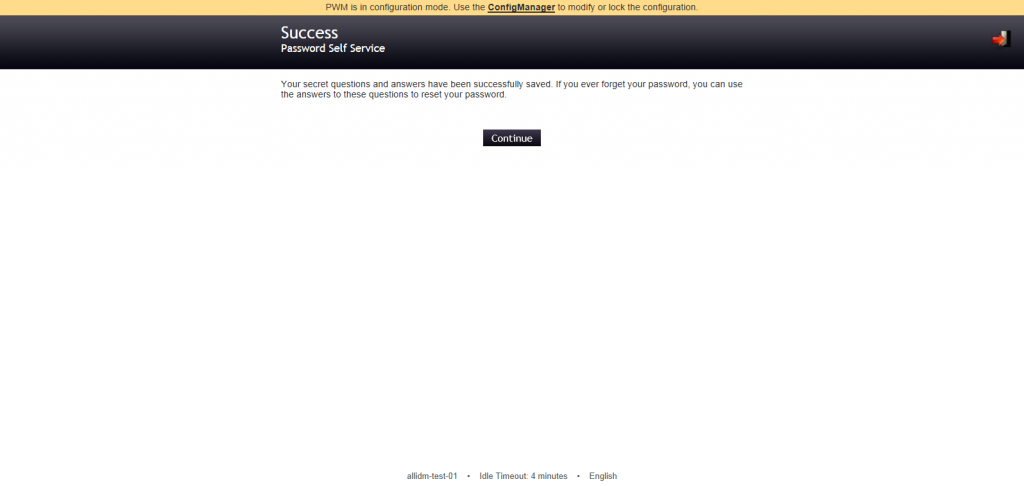
Save the questions & confirm the question and PWM will display a screen with the confirmation.
Click continue to logout.
9 things you need to know about Quest One Password Manager
- Installation Folder
%systemdrive%\Program Files\Quest Software\Quest One Password Manager
- The configuration data is stored locally in the following folder:
%systemdrive%\ProgramData\Quest Software\Password Manager
- Password Manager configuration is stored in the following files:
- local.storage
- shared.storage
- Password Manager Service is called QPM Service
- Password Manager uses the scheduled task and the _QPMStorageContainer account to copy and distribute configuration data from one Password Manager instance to another, and to synchronize data among instances for consistency.
- _QPMStorageContainer is the configuration storage account that is automatically created in the Users container of the managed domain, when you add a managed domain to a user scope. This account is used for storing a copy of Password Manager configuration data and replicating the configuration changes between Password Manager instances.
- There is only one ’_QPMStorageContainer‘ Active Directory object per Quest Password Manager install.
- By defualt, Quest One Password Manager creates a local group named QPMAdmin on the local server where the QPM Service is installed and gives directory permissions to the QPMAdmin virtual directory in IIS.
- To grant permissions to a user account for gaining access to the QPMAdmin website, simply add the user account to the QPMAdmin local group on the Server where the Quest One Password Manager Administrator site is installed.
Which macros are available in Open Source Password Self Service for LDAP directories (PWM)?
The following macros are available:
| @LDAP:<attributeName>@ | Replace with LDAP value of <attributeName> |
| @LDAP:DN@ | Replace with LDAP value of user’s Distinguished Name |
| @User:PwExpireTime@ | Time user’s password will expire in PWM default format. |
| @User:PwExpireTime:<pattern>@ | Time user’s password will expire where <pattern> is a SimpleDateFormat pattern |
| @User:DaysUntilPwExpire@ | Number of days until the user’s password will expire |
| @User:ID@ | User’s UserID (if authenticated) |
| @PWM:InstanceID@ | Instance ID of the PWM application |
| @PWM:CurrentTime@ | Current time in default PWM format. |
| @PWM:CurrentTime:<pattern>@ | Current time where <pattern> is a SimpleDateFormat pattern |
| @PWM:SiteURL@ | URL of the site (http://www.example.com/pwm) |
| @PWM:SiteHost@ | Hostname of the site (www.example.com) |
To use a macro, just place the macro into the configuration value such as:
Dear, @LDAP:givenName@, Thank you for your activity today, @PWM:CurrentTime:EEE, MMM d, yyyy@.
This macro will then be expanded to:
Dear, John, Thank you for your activity today, Wed, Jul 4, 2001.
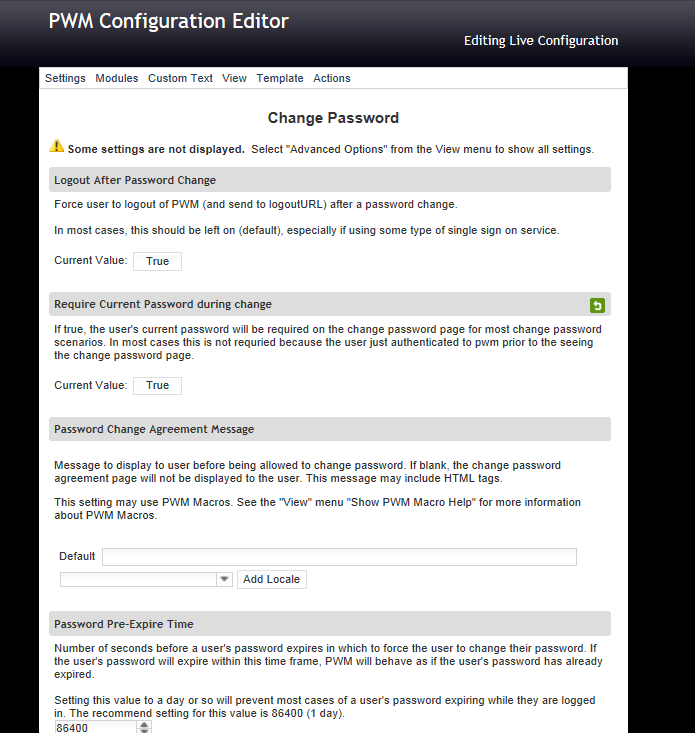
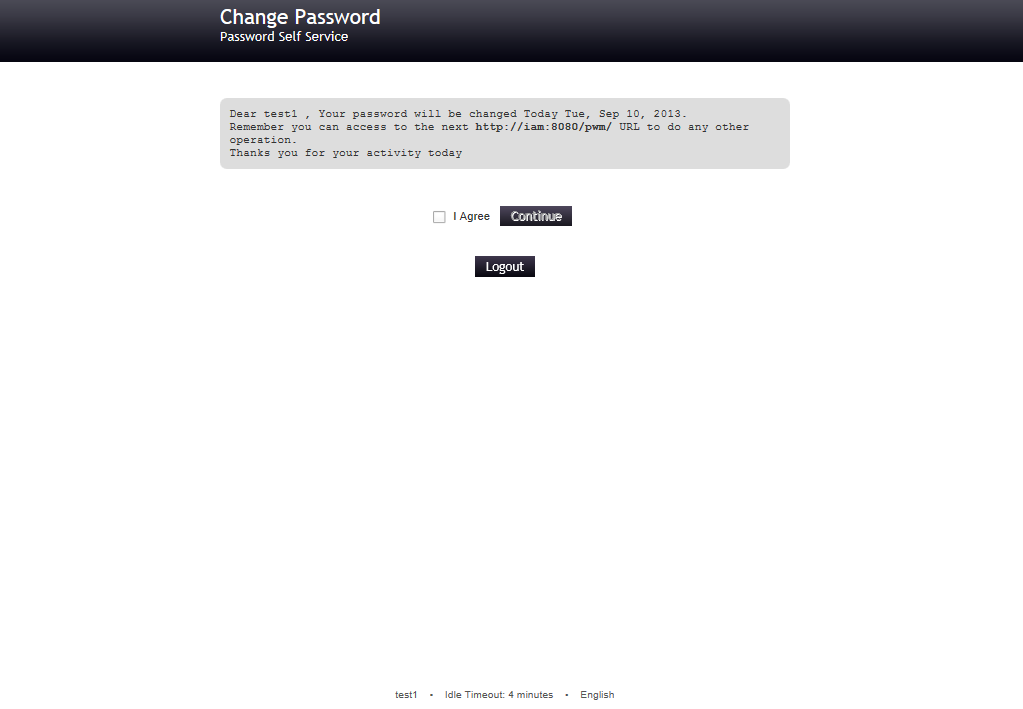
Display a Password Change Agreement Message in Open Source Password Self Service for LDAP directories (PWM)
Follow the next steps to include you customized Password Change Agreement Message:
1. Select or go to the PWM Configuration Editor
2. Select Modules > Change Password
3. Go to the Password Change Agreement Message section
4. By default this section do not include any message.
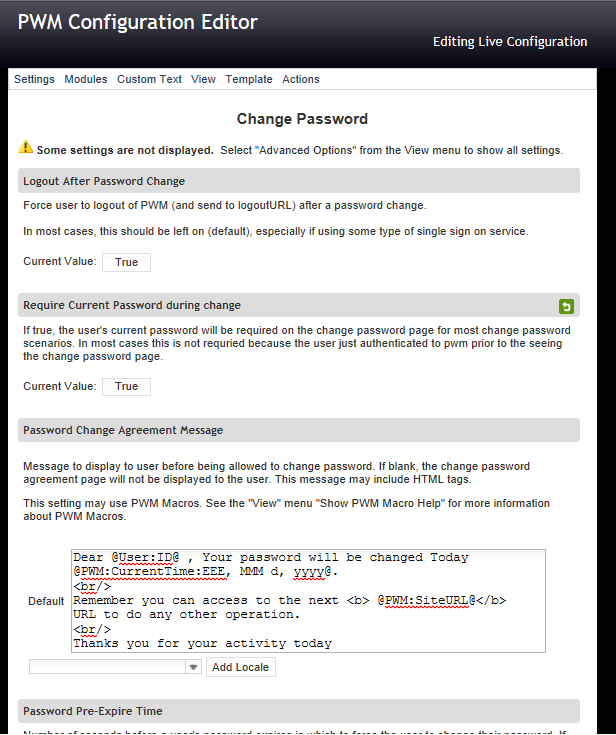
5. In the default textbox include your agreement message. Remember you can use plain text, html and PWM macros.
Dear @User:ID@ , Your password will be changed Today @PWM:CurrentTime:EEE, MMM d, yyyy@.
Remember you can access to the next @PWM:SiteURL@ URL to do any other operation.
Thanks you for your activity today
5. Save your changes and review the output.
a. Login with a test account
b. Select Change Password
c. Your Custom message is displayed before to proceed for a password change.
d. Change your password
e. Wait for the system for Change your password.
f. A Success message is displayed. Click Continue to finish.